With Qualys, you can quickly determine what’s actually running in the different parts of your network—from your perimeter and corporate network to virtualized machines and cloud services such as Amazon EC2. Uncover unexpected access points, web servers and other devices that can leave your network open to attack.
Visually map your network with our graphical host map
Prioritize your remediation by assigning a business impact to each asset
Identify which OS, ports, services and certificates are on each device on your network
Organize hosts to match the structure of your business—e.g., by location, region, and company department
Control which hosts can be scanned by which users
Continuously monitor your perimeter for unexpected changes with our optional Continuous Monitoring service
Dynamically tag assets to automatically categorize hosts by attributes like network address, open ports, OS, software installed, and vulnerabilities found
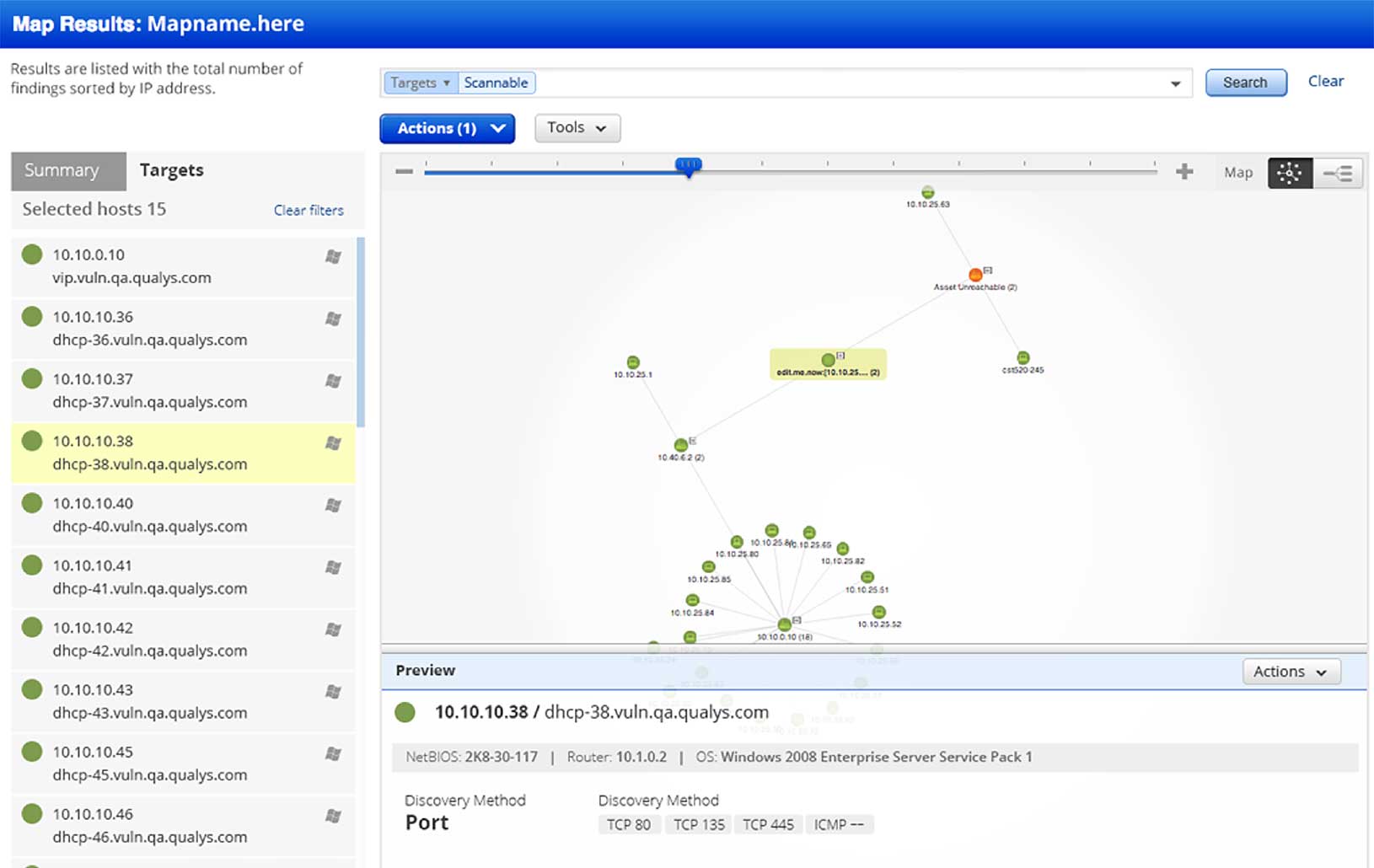
Scan systems anywhere from the same console: your perimeter, your internal network, and cloud environments (such as Amazon EC2). Since Qualys separates scanning from reporting, you can scan deeply and then create custom reports showing each audience just the level of detail it needs to see.
Select target hosts by IP address, asset group or asset tag
Scan manually, on a schedule, or continuously
Scan behind your firewall securely with Scanner Appliances, remotely managed by Qualys 24/7/365
Scan complex internal networks, even with overlapping private IP address spaces
Securely use authentication credentials to log in to each host, database or web server
Scan in Amazon EC2 without filling out request forms—Qualys is pre-approved
Save time with our Six Sigma accuracy rate—no more chasing after false positives
Store configuration information offsite with secure audit trails
Using Qualys, you can identify the highest business risks using trend analysis, Zero-Day and Patch impact predictions.
Track vulnerabilities over time: as they appear, are fixed, or reappear
Monitor certificates deployed throughout your network—see what’s about to expire, which hosts they are used on, what their key size is, and whether or not they are associated with any vulnerabilities
Put critical issues into context with the Qualys’ industry-leading, constantly updated KnowledgeBase
See which hosts need updates after Patch Tuesday every month
Examine your network’s vulnerabilities over time, at different levels of detail, instead of just single snapshots
Predict which hosts are at risk for Zero-Day Attacks with the optional Qualys Zero-Day Risk Analyzer
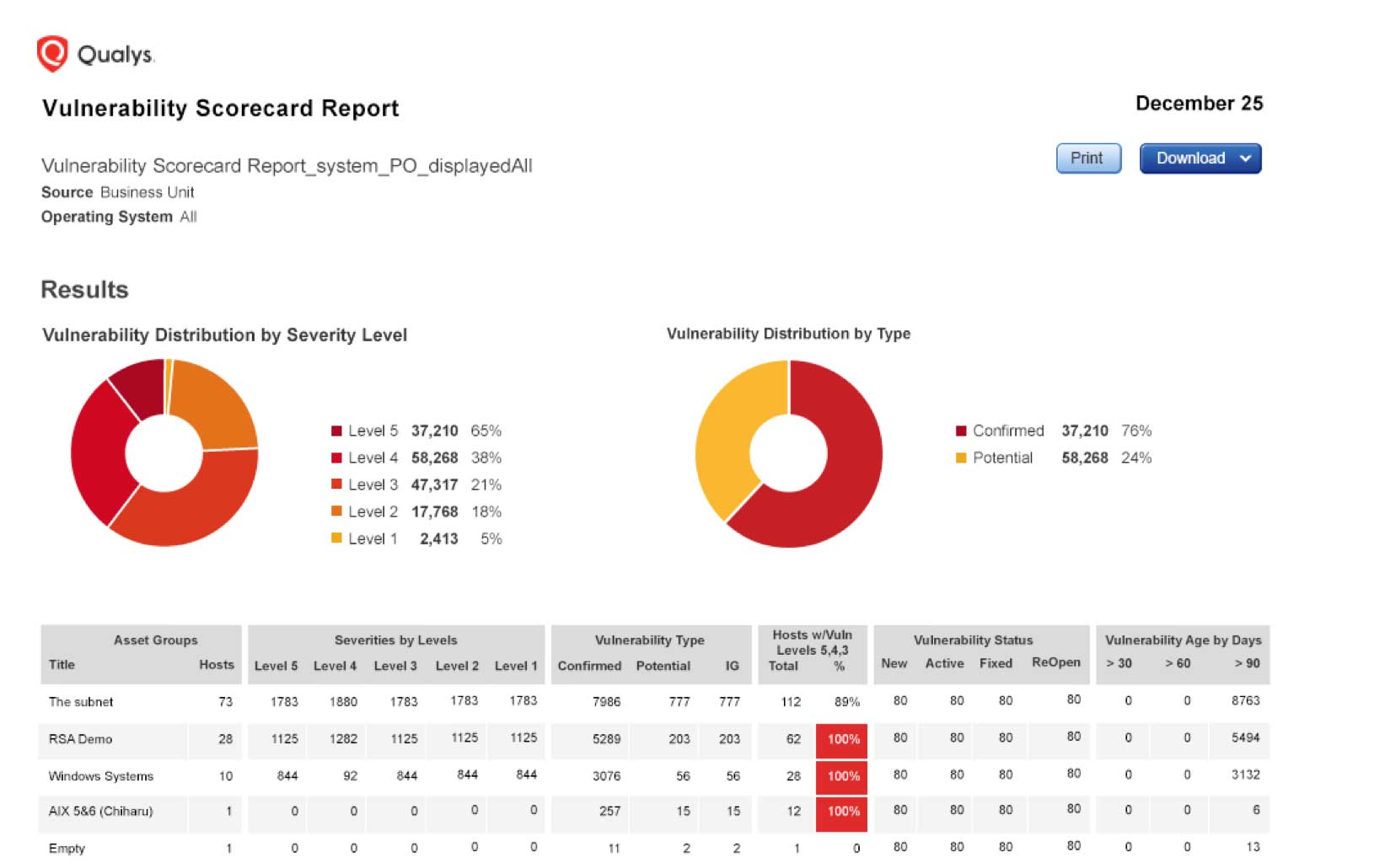
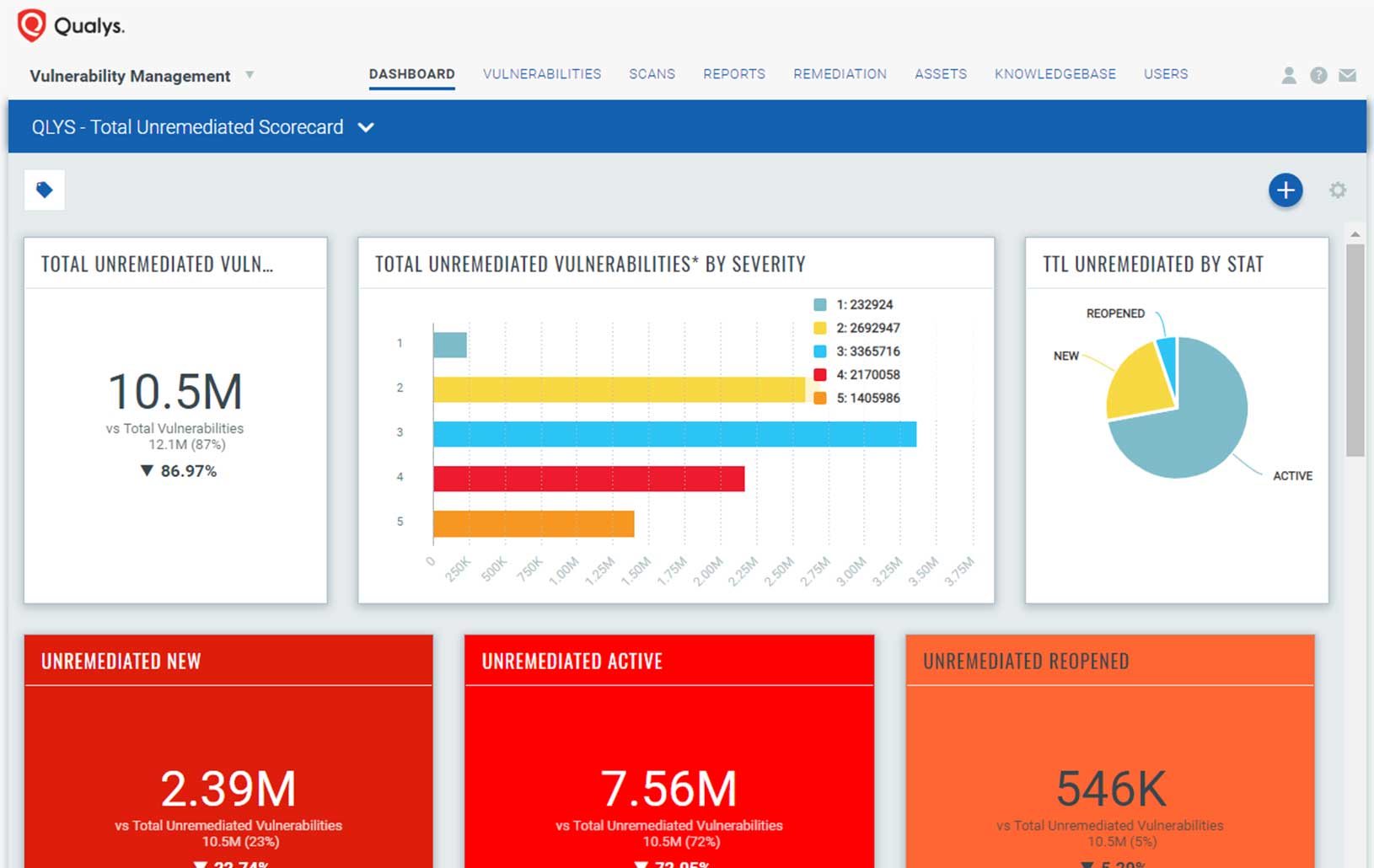
Qualys tracks the disposition of each vulnerability on each host over time. This helps you document the actions taken in response to each vulnerability and monitor the effectiveness of your remediation efforts.
Automatically generate and assign remediation tickets whenever vulnerabilities are found
Get consolidated reports of which hosts need which patches
Integrate with third-party IT ticketing systems
Manage exceptions when a vulnerability might be riskier to fix than to leave alone
Exceptions can be set to automatically expire after a period of time for later review
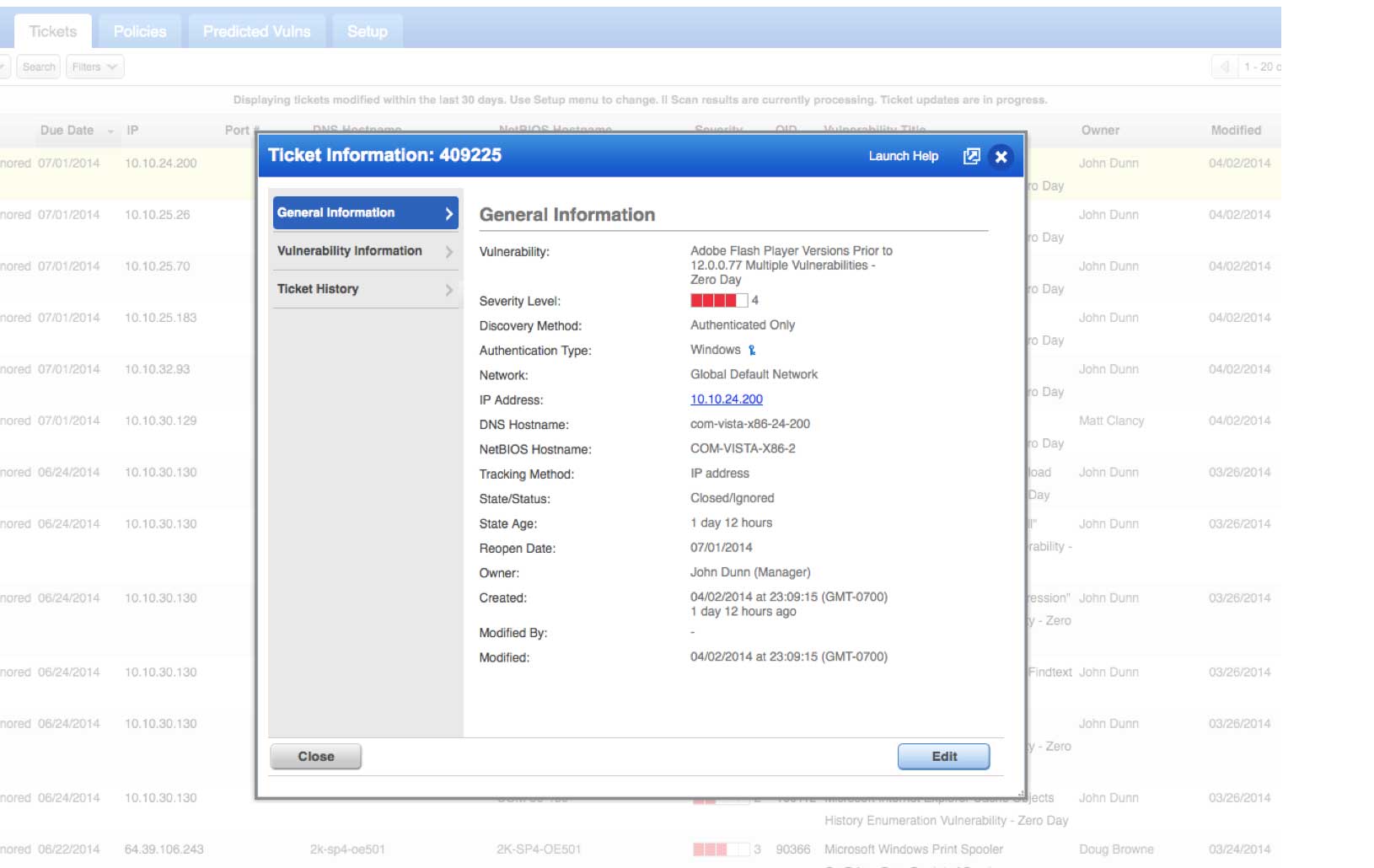
Qualys’ ability to track vulnerability data across hosts and time lets you use reports interactively to better understand the security of your network. Use a library of built-in reports, change what’s shown or choose different sets of assets — all without having to rescan. Reports can be generated on demand or scheduled automatically and then shared with the appropriate recipients online, in PDF or CSV.
Create different reports for different audiences—from scorecards for executives, to detailed drill-downs for IT teams
Document that policies are followed & lapses get fixed
Provide context & insight about each vulnerability, including trends, predictions, and potential solutions
Track ongoing progress against vulnerability management objectives
Share up-to-the-minute data with GRC systems & other enterprise applications via XML-based APIs
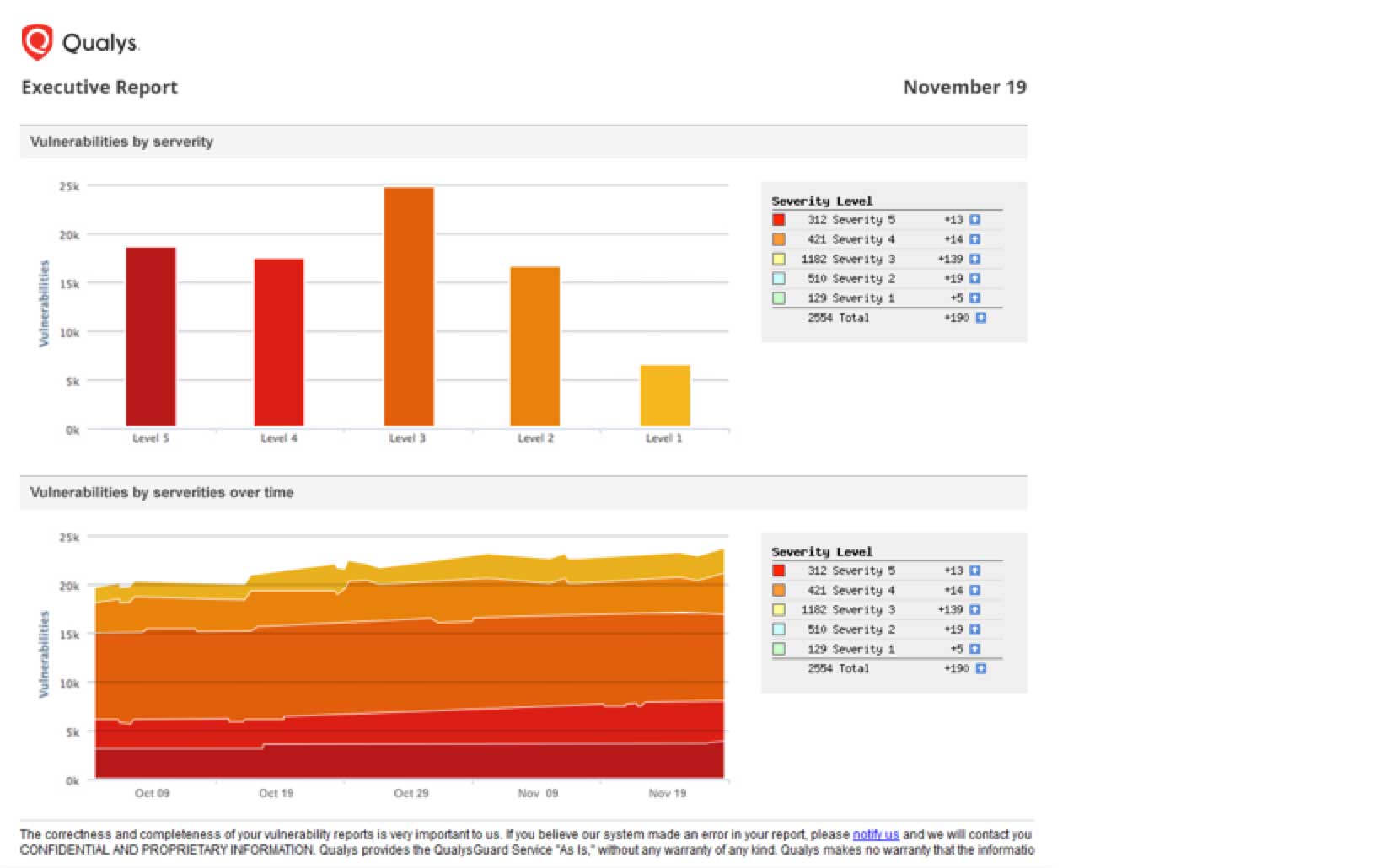
Qualys VM’s dashboard has been improved by making it more customizable as part of our overall efforts to add more flexibility to the platform. With the new VM dashboard, you can:
Conduct searches and create widgets without leaving the VM app
Build vulnerability widgets with vulnerability counts, in addition to asset widgets with asset counts
Use new search filters to quickly build queries, so you don’t have to type up long queries in the search box
Replace current reports with live widgets, and enjoy benefits like finding where a CVE is across your environment very quickly without having to run a report
The #1 Vulnerability Management solution expands to establish a new, game-changing category
Learn more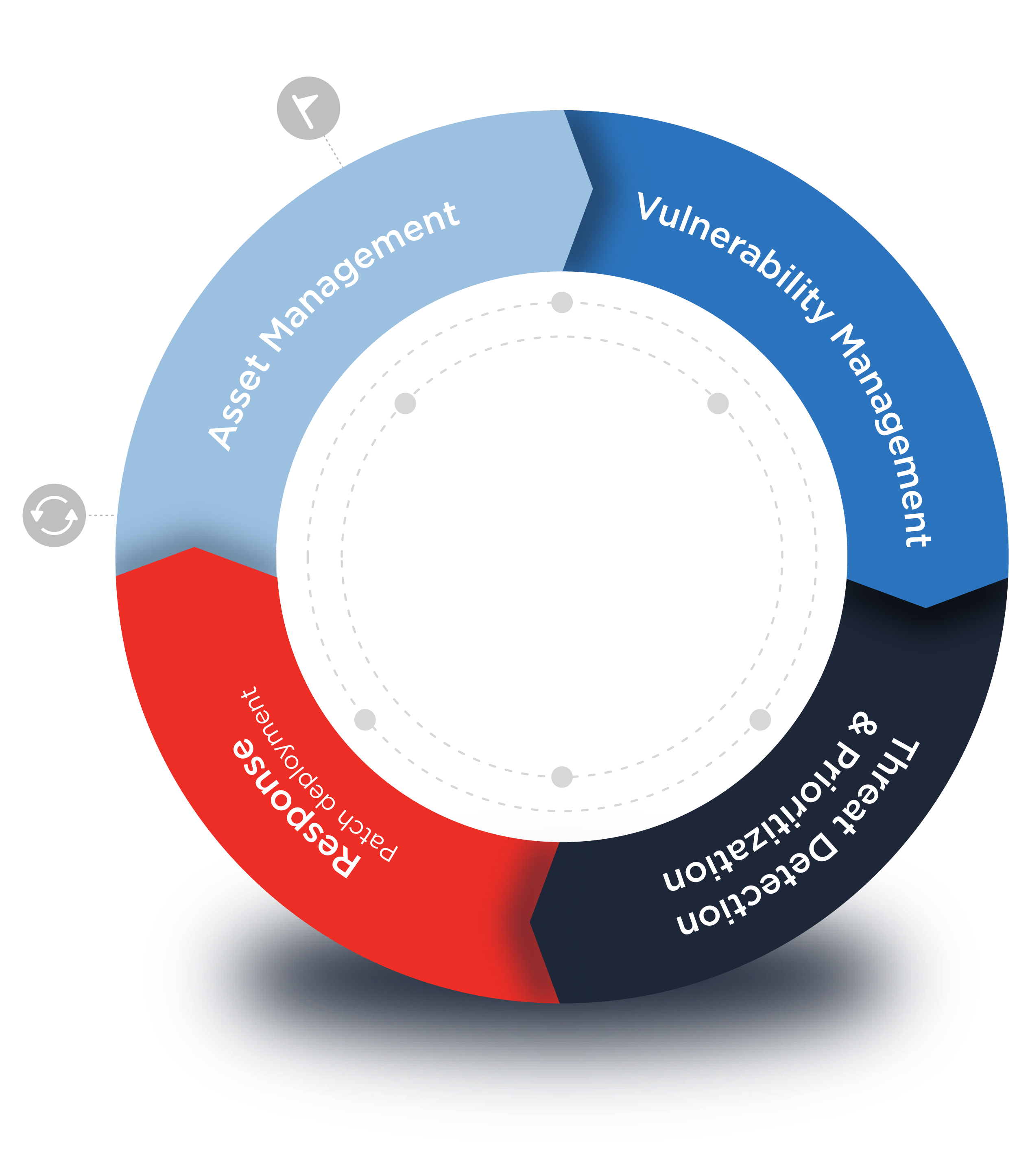
VMDR with Transparent Orchestration

Là phương châm làm việc của chúng tôi

10 năm
kinh nghiệm

Đổi sản phẩm
7 ngày


Giá luôn
rẻ nhất

Giao dịch
an toàn