Organizations often overlook improperly configured IT assets, underestimating their security and compliance risks. In fact, misconfigurations — like keeping default passwords, improper access control settings, weak encryption configuration, or insecure application deployment — are a major vector for breaches. Qualys PC automates the process of assessing security configurations, starting with configuring policies.
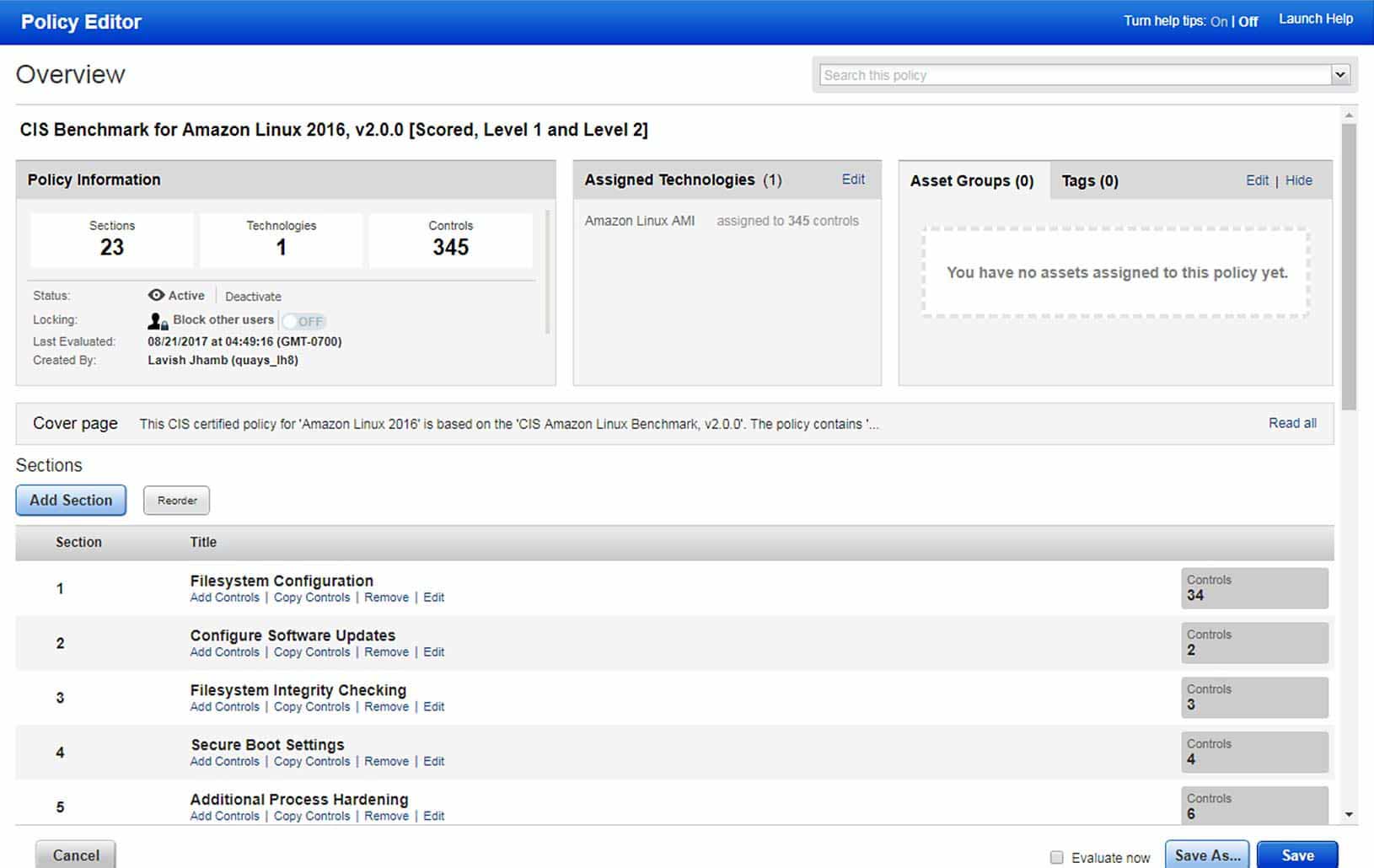
Qualys PC’s interactive editor automatically organizes controls according to the technologies associated with each policy. Its search engine quickly finds relevant controls according to attributes such as name, category, framework, and others.
Test controls immediately without rescanning or reporting
While setting up a control within Qualys, test the specified configuration, so you don’t have to run a new scan or generate a special report each time you edit a control. Qualys gives you a list of relevant hosts to choose from and shows you what values were gathered
Select from a rich library of controls for OSes, network devices, databases & apps
Qualys’ extensive, continually updated library of more than 15,000 checks spans more than 50 technologies. Controls can be filtered and selected according to multiple attributes, including: description keywords and category
Monitor the integrity of files and watch for changes
Qualys can monitor arbitrary files on Windows and Unix/Linux hosts for changes so that unexpected modifications can be caught quickly
Create custom controls without writing code or scripts
Extend Qualys’ controls easily without programming. On Unix/Linux and Windows hosts, attributes of files and directories can be examined with just a few clicks. On Windows hosts, checks for registry entries, share permissions, and WMI queries can also be added quickly
See how controls relate to critical frameworks and regulations
Qualys provides context information for each built-in control such as the standards frameworks to which the control applies, including: CIS, COBIT, ISO 17799 & 27001, NIST SP800-53, ITIL v2, HIPAA, FFIEC, NERC-CIP
Make policies active or inactive
Every policy in your account is in active or inactive state. Inactive policies will not be scanned or reported on. By default polices are marked active. You may want to hide a new policy while you’re working on it, or an existing one you’re editing, and then publish it at a later time
With Qualys PC, you can scan systems anywhere from the same console. You can select target hosts by IP address, asset group or IP range. After scanning deeply, you can create custom reports for each audience with the appropriate level of detail.
Scan quickly & efficiently
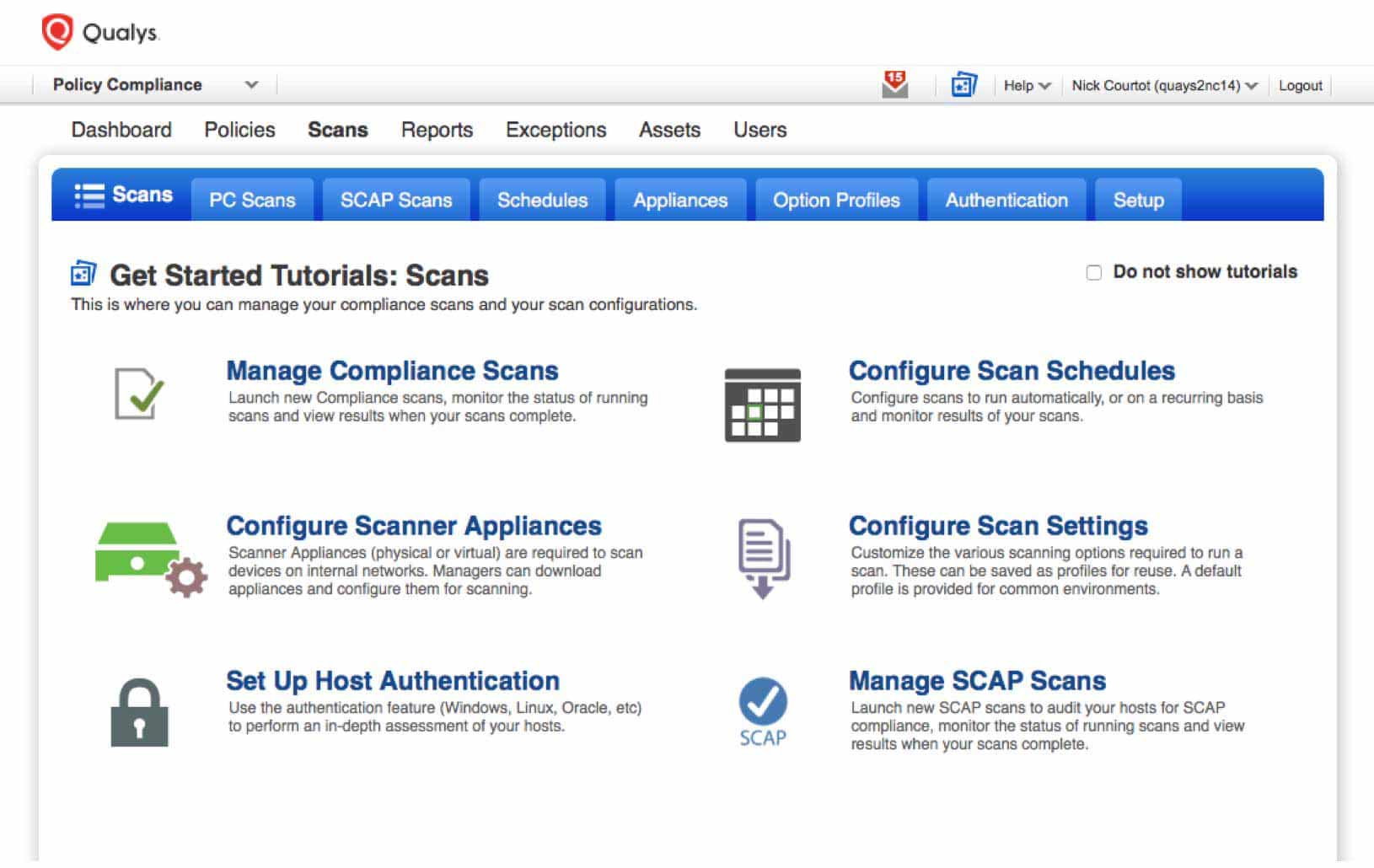
Qualys PC works unobtrusively in even the largest networks. Use your existing asset groups to select systems to scan. Do internal network scans in parallel using multiple appliances to accelerate scanning and prevent network bottlenecks
Scan behind your firewall securely with Scanner Appliances managed by Qualys
Scan your internal networks seamlessly with physical and virtual Qualys Scanner Appliances. Efficiently monitor internal hosts, network devices, databases and other assets without opening inbound firewall ports or setting up special VPN connections
Store configuration information offsite with secure audit trails
As a cloud service, Qualys provides a trusted, independent location for securely storing critical configuration information and tamper-resistant audit trails
Scan on demand or on a schedule
Qualys gives you the flexibility to scan whenever you want. You can launch scans with a click to manually check desired hosts, or schedule recurring scans with specific durations to match your maintenance windows
Assess deeply with authentication scans
Qualys can securely use authentication credentials to log in to each host, database or web server. For added control, Qualys can pull passwords dynamically from 3rd-party credential management systems and use privilege escalation systems such as “sudo”
Do continuous compliance with Qualys Cloud Agents
Turn Qualys PC into a real-time compliance assessment solution with the groundbreaking Cloud Agents. These lightweight agents are always up to date and require no credential management nor complex remote access through the firewall. They monitor assets around the clock, even if they’re offline
Qualys PC automates the labor-intensive process of checking settings on each machine in your network. By helping you address violations quickly, before they get too far out of hand, Qualys PC makes remediation efforts more predictable and avoids last-minute emergencies during audits.
Manage exceptions via a documented approvals process
By eliminating configuration fire drills, Qualys PC shifts the focus of your efforts to managing exceptions for specific hosts and situations. Qualys provides a documented, repeatable workflow for requesting, evaluating and approving exceptions. Approvals can be temporary, allowing issues to be automatically revisited after a specified length of time.
Know that audits will show compliance, not uncover violations
Know whether your IT systems are compliant with configuration mandates. Issues can be resolved early, reducing or eliminating the chances for failed IT audits. Instead, with Qualys PC audits validate that you are following the kinds of best practices that reassure auditors.
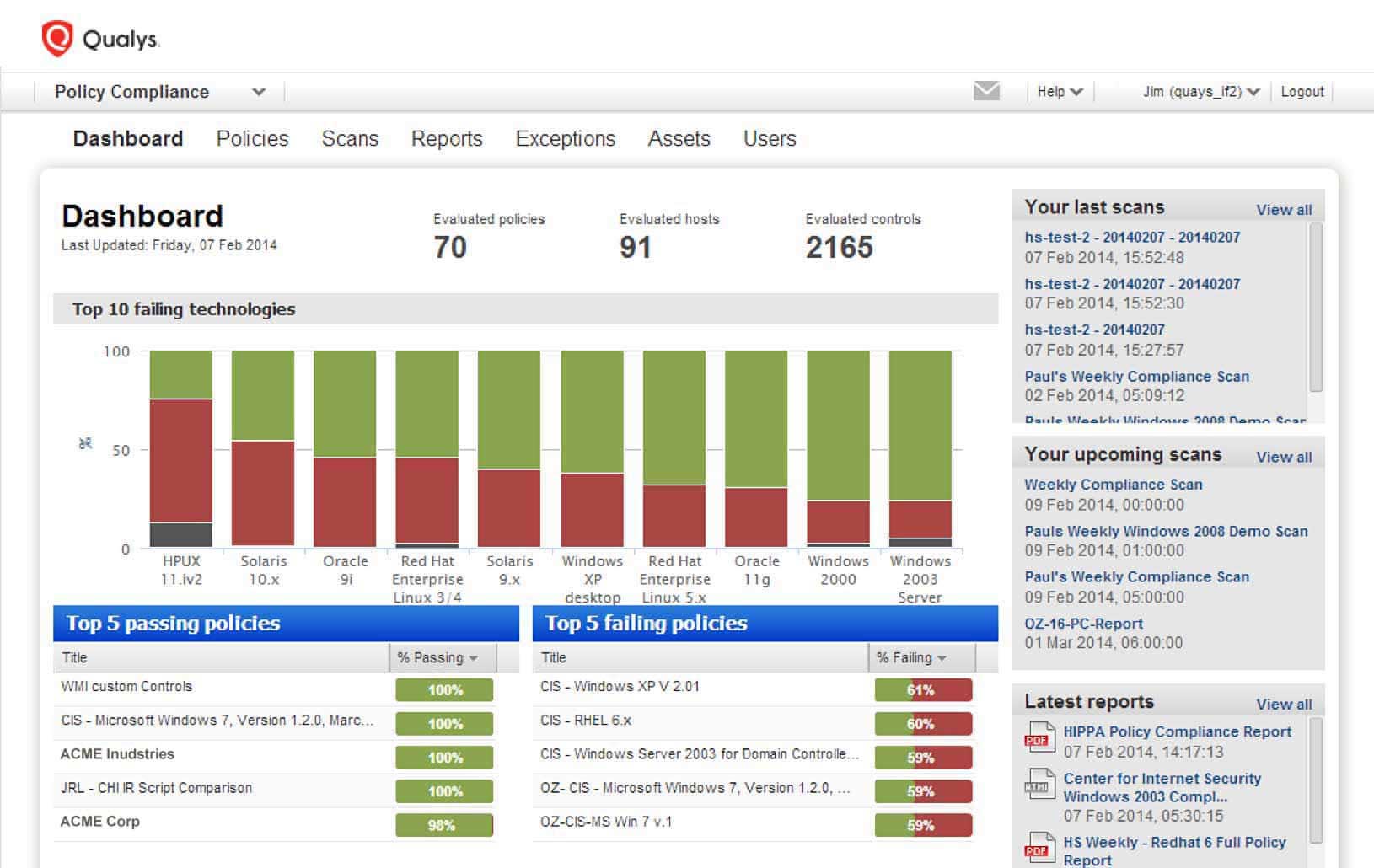
It’s essential to collect and analyze compliance data in order to evaluate and fine-tune IT security controls. Qualys PC gives you comprehensive compliance data so you can prioritize remediation and maintain all different stakeholders informed, including IT, business executives, risk managers and auditors.

Là phương châm làm việc của chúng tôi

10 năm
kinh nghiệm

Đổi sản phẩm
7 ngày


Giá luôn
rẻ nhất

Giao dịch
an toàn